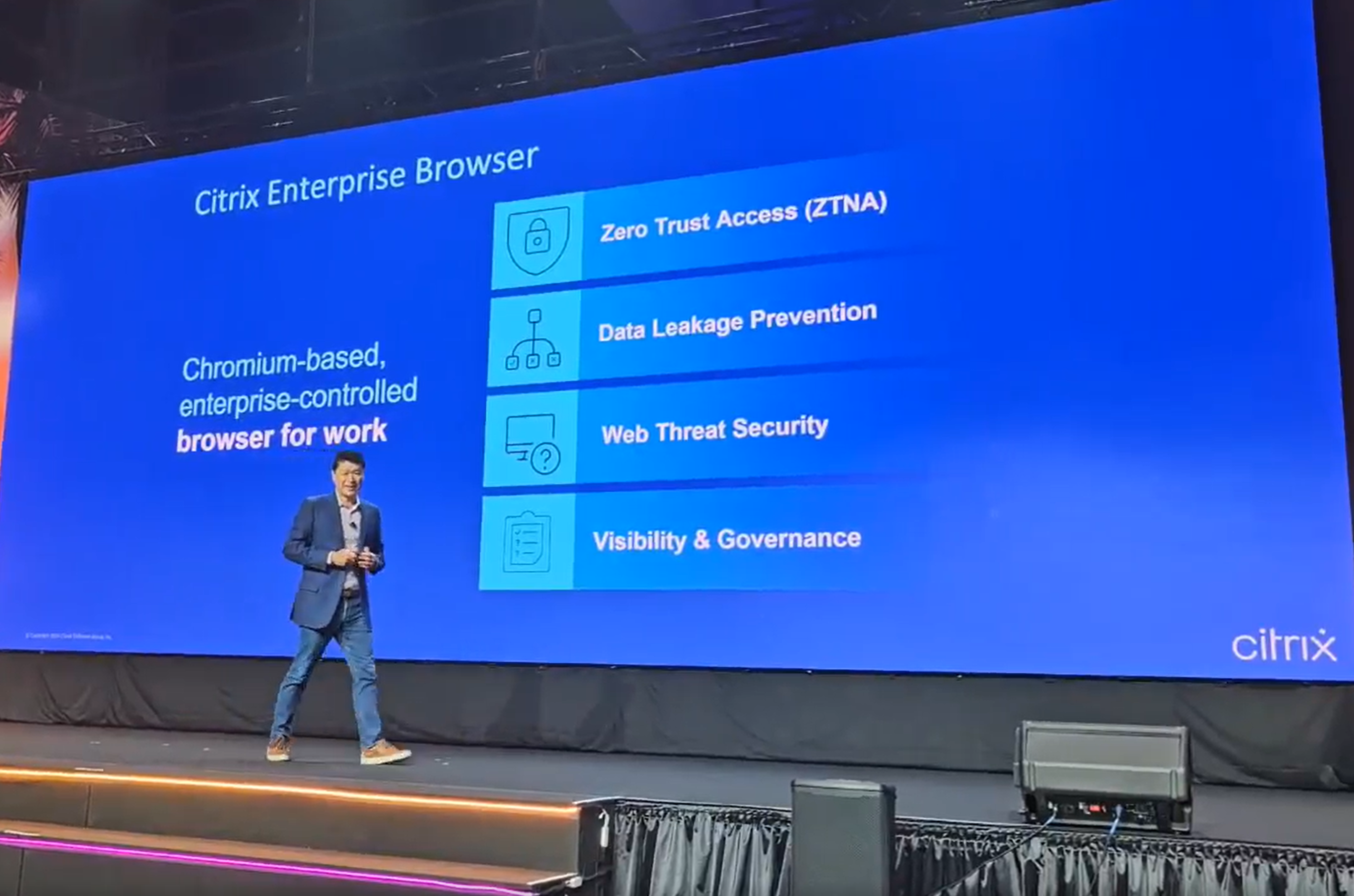
Building upon the robust security of Linux thin clients, Citrix is thrilled to announce the expansion of its Enterprise Browser offerings to Linux, marking a significant step in our access security platform expansion strategy. This empowers organizations to further secure access to web and SaaS applications, particularly for environments reliant on Linux thin clients, which are already locked down by design and managed by thin client vendors.
This release, currently available as a private tech preview, comes packed with powerful features that are waiting for you to explore. As part of this preview, let’s dive into its advanced capabilities, particularly in the context of enhanced security for Linux thin clients:
Zero Trust Network Access Solution:
Implementing Zero Trust Network Access (ZTNA) is essential for IT administrators. Without it, organizations face increased vulnerability to cyber threats like phishing and data breaches. Traditional access methods lack granularity, leading to over privileged access and security gaps. Now let’s look at Citrix’s ZTNA solution.
Citrix’s ZTNA solution goes beyond traditional access methods by implementing granular access controls and Data Loss Prevention (DLP) functionalities. This empowers organizations to define and enforce security policies specifically for web and SaaS applications accessed through the Enterprise Browser on Linux thin clients.
You can securely access web apps through Citrix Secure Private Access without the need of VPN, whether you choose the on-premise or cloud solution. With Secure Private Access, you can enforce security controls such as clipboard restrictions, download/upload/printing restrictions, and display watermarks to your web and SaaS apps.
- Clipboard restriction: Disables cut, copy, and paste operations between the app and the endpoint’s clipboard.
- Download restriction: Disables the ability to download from within web and SaaS apps or copy files from the browser.
- Upload restriction: Disables the ability to upload files
- Printing restriction: Disables the ability to print from within the app.
App protection:
Threats like keyloggers and screen capturing loom large, putting user privacy and confidential information at risk. That’s where robust app protection comes in, ensuring data integrity and earning user trust. Luckily, with Citrix app protection in the Enterprise browser, we’ve got you covered against these lurking threats.
Restrict keylogging: Shields users from sneaky keyloggers while accessing the web applications in the enterprise browser on Linux.
Restrict screen capturing: Stops anyone from taking screenshots or recording your screen while using the app this policy applies to. Just make sure the protected tab stays visible in your browser window to keep your data secure.
Citrix Enterprise Browser was announced as a Public Tech Preview last week in one of the EUC events. Citrix Enterprise Browser is compatible with all the Linux thin client vendor OS
In conclusion, Citrix Enterprise Browser’s expansion to Linux brings robust security features like zero-trust network access and app protection, ensuring a safer browsing experience for your enterprise web and SaaS applications. With seamless integration and enhanced monitoring capabilities, administrators can enjoy complete visibility and protection against threats. Embrace this advancement for a secure and productive browsing environment.
We are working very closely with our thin client partners to start integrating the new Enterprise browser on Linux in their thin clients to be ready when the product is generally available. Please inquire us or your thin client partner for more details.
Disclaimer: This publication may include references to the planned testing, release and/or availability of Cloud Software Group, Inc. products and services. The information provided in this publication is for informational purposes only, its contents are subject to change without notice, and it should not be relied on in making a purchasing decision. The information is not a commitment, promise or legal obligation to deliver any material, code, or functionality. The development, release, and timing of any features or functionality described for products remains at the sole discretion of Cloud Software Group, Inc.