Many Citrix customers with Machine Creation Services (MCS) catalogs that use Azure have told us they want to deploy the Azure Monitor Agent (AMA) on their MCS-created VDAs to align with their enterprise monitoring standards. Unfortunately, simply provisioning a machine catalog with the AMA installed on the master image did not yield unique monitoring data for child VDAs in Azure Monitor. As a result, all child VDAs would report to Azure Monitor with the same parent ID.
Until now.
Citrix has released a new feature that enables MCS created VDAs that are hosted on Azure with the Azure Monitor Agent installed as an extension and allowing the ability to uniquely identify VDAs in monitoring data. This blog post will provide an overview of this new capability and show you how to do it step by step.
What is the Azure Monitor Agent?
Azure Monitor is Azure’s monitoring service, which gathers, stores, and analyzes deployment metrics. The Azure Monitor agent is used to collect monitoring data from guest operating systems and to send that data to Azure Monitor.
Azure Monitor uses data collection rules (DCRs) to define which data an administrator wants each agent to collect and from which Azure resources. You can install the AMA in several different ways, including as an extension defined in an Azure Resource Manager (ARM) template. In turn, an ARM template can be generated via either a template spec or a VM. You can find the full list of prerequisites for installing the AMA in the Microsoft documentation.
Prerequisites
To get started with setting up Azure Monitor on your MCS catalogs, you’d need to take care of the following prerequisites:
Set the Necessary Permissions
The following Azure permissions are required for the service principal used with MCS. You should follow the security principle of least privilege when assigning permissions. These permissions are detailed in the Citrix DaaS product documentation.
Microsoft.Compute/virtualMachines/extensions/read
Microsoft.Compute/virtualMachines/extensions/write
Microsoft.Insights/DataCollectionRuleAssociations/Read
Microsoft.Insights/dataCollectionRuleAssociations/write
Microsoft.Insights/DataCollectionRules/Read
Remove Any VM Extensions from the MCS Master Image
Microsoft strongly recommends removing VM extensions from an existing machine before creating a new machine from it, per their documentation. If you don’t, leftover files on the master VM can result in unexpected behavior on child VMs. In our case, when using a machine as a master image for MCS, we should remove any extensions from the master image. Once the necessary child VMs are provisioned, you can reinstall any extensions.
Create a Log Analytics Workspace
When you collect logs and performance data from monitored resources, the information is stored in one or more Log Analytics workspaces. To use this feature and create a data collection rule, at least one workspace must be created. A workspace has a unique workspace ID and resource ID. The workspace name must be unique for a given resource group. Refer to the Microsoft documentation for guidance on creating a workspace.
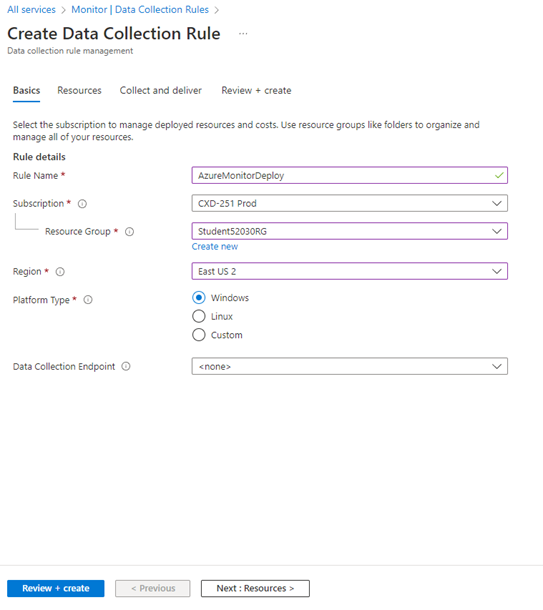
Setup Data Collection Rule
The Azure Monitor Agent (AMA) uses Data Collection Rules (DCR) to manage the mapping between the resources, such as VMs, and data sources, like Azure Monitor Metrics and Azure Monitor Logs. Follow Microsoft documentation for steps on how to set up one.
The screenshot below shows how an admin can add a Data Collection Rule from within the Azure console:
Few things to note about Data Collection Rule:
- Data collection rule setup with a Microsoft Sentinel data connector can be used in the same way as a regular rule.
- For a rule in a different subscription than the provisioning setup (machine profile, catalog VMs, NIC, etc.), you may need to link the 2 subscriptions as mentioned in this documentation.
For information on the best practices for data collection rule creation, see Best practices for data collection rule creation and management in Azure Monitor.
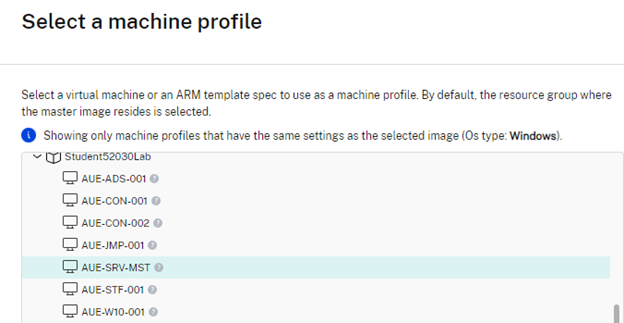
Setup Machine Profile
Azure Monitor Agent extension can only be installed through using a machine profile. Machine Profile allows for having one place to specify all virtual machine settings, instead of having to pass the settings individually when creating or updating a catalog. For Azure, it can provide hardware details (service offering, disk tier), networking settings (subnets, security groups) and enable features like disk encryption, accelerated networking, and availability zones that will be carried through to created machines.
More information about Machine Profile can be found here.
Approval for Your VM Extensions (Optional)
Extensions defined in the machine profile VM or template spec are currently ignored unless they are explicitly approved. With this feature, Citrix has explicitly defined the AMA for Windows and Linux as Citrix-defined and approved extensions. However, customers may have other VM extensions applied. Some VM extensions can be exported as documented here. For other extensions, they need to be manually placed back into the ARM template. To verify if the VM extensions are correctly approved, run Get-ProvMetadataConfiguration and review the output per the example below.
PS C:\Windows\system32> Get-ProvMetadataConfiguration
| PluginType | ConfigurationName | ConfigurationValue | CitrixDefined |
|---|---|---|---|
| AzureRM Extension | AzureMonitorWindowsAgent | True | True |
| AzureRM Extension | AzureMonitorLinuxAgent | True | True |
| AzureRM Extension | CustomScriptExtension | False | False |
How to install Azure Monitor Agent
Link Machine Profile to Data Collection Rule
When using VM as a machine profile,
- Go to the data collection rule in Azure portal.
- Under Resources, add the VM that we just set up as the machine profile.
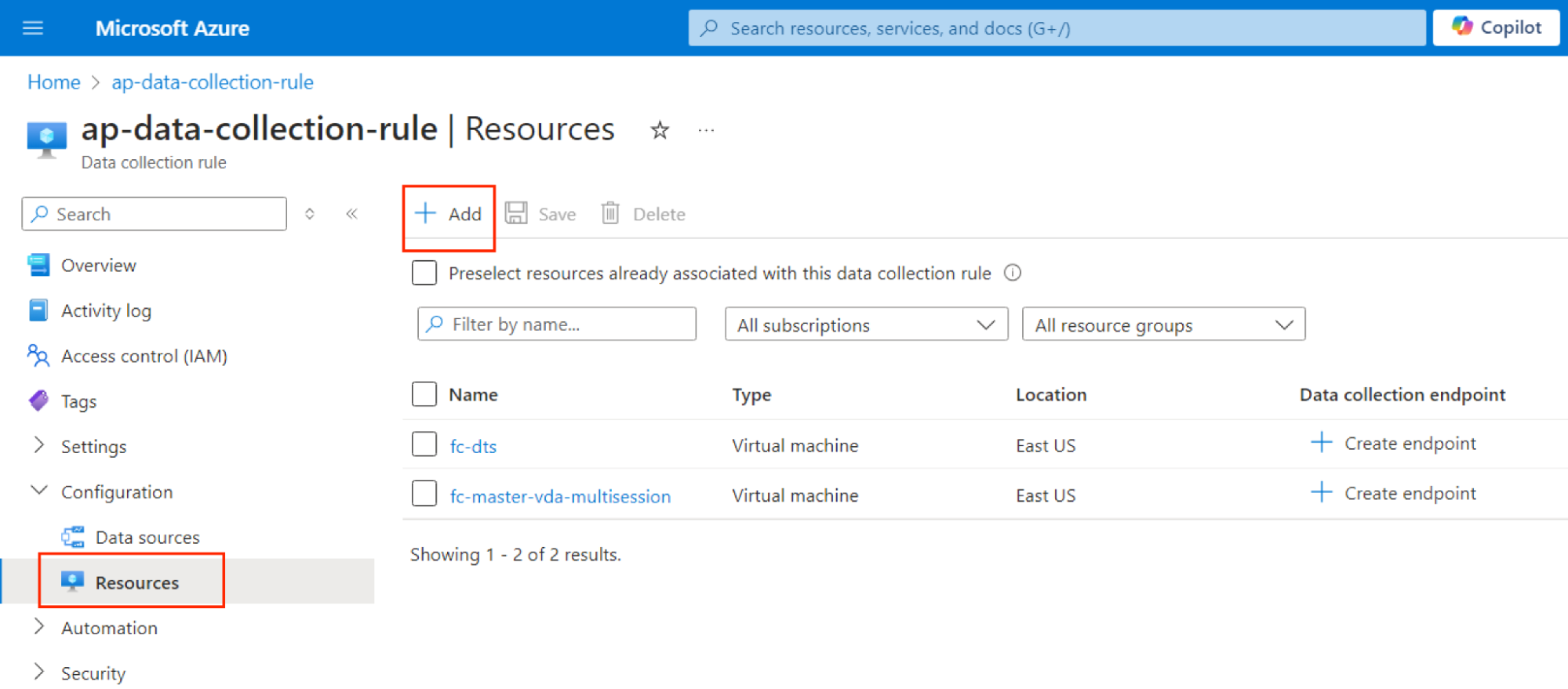
- At this point, an automatic installation of AMA would be invoked on the VM.
- You can then verify this by going to the machine profile VM, navigating to ‘Extensions + applications’ under Settings in the navigation menu, and then confirming that the appropriate extension is listed.
- For Windows VMs, the extension would be AzureMonitorWindowsAgent and for Linux, it would be AzureMonitorLinxuAgent.
Alternatively, if you’re using template spec as machine profile, add the following sections to the template:
{
“type”: “Microsoft.Compute/virtualMachines/extensions”,
“apiVersion”: “2022-03-01”,
“name”: “<vm-name>/AzureMonitorWindowsAgent”,
“dependsOn”: [
“Microsoft.Compute/virtualMachines/<vm-name>”
],
“location”: “<azure-region>”,
“properties”: {
“publisher”: “Microsoft.Azure.Monitor”,
“type”: “AzureMonitorWindowsAgent”,
“typeHandlerVersion”: “1.0”,
“autoUpgradeMinorVersion”: true,
“enableAutomaticUpgrade”: true
}
},
{
“type”: “Microsoft.Insights/dataCollectionRuleAssociations”,
“apiVersion”: “2021-11-01”,
“name”: “<association-name>”,
“scope”: “Microsoft.Compute/virtualMachines/<vm-name>”,
“dependsOn”: [
“Microsoft.Compute/virtualMachines/<vm-name>”,
“Microsoft.Compute/virtualMachines/<vm-name>/extensions/AzureMonitorWindowsAgent”
],
“properties”: {
“description”: “Association of data collection rule. Deleting this association will break the data collection for this Arc server.”,
“dataCollectionRuleId”: “/subscriptions/<azure-subscription>/resourcegroups/<azure-resource-group>/providers/microsoft.insights/datacollectionrules/<azure-data-collection-rule>”
}
}
Select Machine Profile for a Catalog
To create a new catalog with AMA, select the machine profile (VM or template spec) that was just setup in Citrix Studio as shown below:
If you’d like to enable AMA on an existing machine catalog, run the following powershell commands:
1. Update Provisioning Scheme with VM or template spec as machine profile
Set-ProvScheme -ProvisioningSchemeName “TEST” -MachineProfile “XDHyp:\HostingUnits\Unit1\machineprofile.folder\Student52030RG.resourcegroup\AUE-machine-profile.vm”
OR
Set-ProvScheme -ProvisioningSchemeName “TEST” -MachineProfile “XDHyp:\HostingUnits\Unit1\machineprofile.folder\Student52030RG.resourcegroup\test-temp-spec.templatespec\1.0.0.templatespecversion”
2. Update ProvVM or existing machines
Set-ProvVMUpdateTimeWindow -ProvisioningSchemeName “TEST” -StartsNow -DurationInMinutes -1
3. Reboot or power on the machines
Azure Monitor extension would then get installed on all provisioned VMs and the provisioned VMs would also show up on the Data Collection Rule under Resources. If all is well, after a few minutes, data will begin to appear in Azure Monitor.
Note: If you’d like to schedule the update for existing machines instead, you may customize Set-ProvVMUpdateTimeWindow as explained here. Also, more info on the Set-ProvScheme command can be found here.
For help troubleshooting, refer to the Microsoft documentation on troubleshooting Azure Monitor Agent and on creating a troubleshooting template.
Get Started Today
MCS now allows the ability to deploy VMs on Azure with the Azure Monitor agent! Organizations which have standardized on Azure Monitor will finally be able to monitor their MCS-managed VMs. Check out our product documentation here to learn more.
Thanks to my colleague Ankita Pagaria, whose contributed her expertise to this blog post.