NOTE: Citrix has now published a full deployment guide around smart cards. I would strongly recommend referring to that guide as it contains a wealth of information.
This guide covers configuring a NetScaler Gateway (NSG), formerly known as Access Gateway Enterprise Edition (AGEE), for CAC authentication to StoreFront (SF). It also applies to PIV cards and SIPR tokens. There is an assumption that the reader is already slightly familiar with both NSG and SF and that both products are already installed in the environment.
Storefront
Enable Authentication Method
- In the StoreFront Console, navigate to Citrix StoreFront->Authentication.
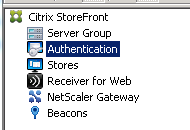
- In the Actions pane, click Add/Remove Methods.
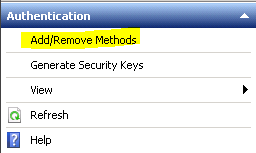
- Check Pass-through from NetScaler Gateway. (NSG was formerly known as Access Gateway Enterprise Edition, AGEE) Click OK.
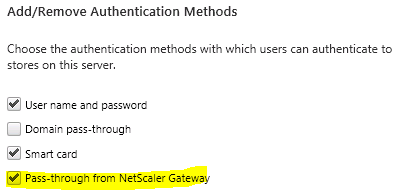
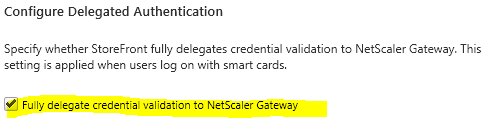
- In the Actions pane, click Configure Delegated Authentication.
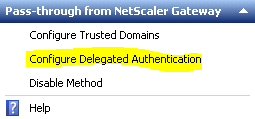
- Make sure Fully delegate credential validation to NetScaler Gateway is checked. Click OK.
Add the NetScaler Gateway
- In the StoreFront Console, navigate to Citrix StoreFront->NetScaler Gateway.
- In the Actions pane, click Add NetScaler Gateway Appliance.
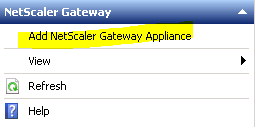
- Enter the information for the environment’s NetScaler Gateway. Take note that this example uses a separate callback vserver. This is because the client certificate setting on the NetScaler will be set to Mandatory. To Use the same vserver it would need to be set to Optional. NOTE: The NSG URL cannot be the same as the Storefront URL. They must be different! Click Next.

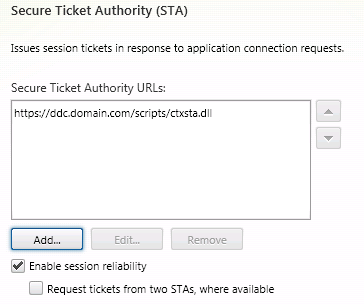
- At the Secure Ticket Authority (STA) windows, click Add and add the STAs for the environment. Set the remainder of the settings as appropriate for the environment. Click Create.
Enable Remote Access for Store
- In the StoreFront Console, navigate to Citrix StoreFront->Stores.
- Select to existing store that is to be configured. In the Actions pane click Enable Remote Access.
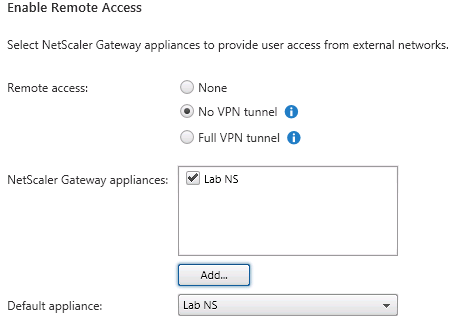
- In the Enable Remote Access window set the Remote Access type to No VPN tunnel. Check the appropriate NSG to use for the Store (new NSGs can also be added here using the Add button). If more than one NSGs were added, select the Default appliance to use for the store. Click OK.
Configuring the NetScaler Gateway
Creating a new virtual server
If there is an existing virtual server to edit, this section can be skipped. Proceed to the Tweaking the Virtual Server section.
- Log into the NetScaler’s web management GUI. All locations given assume the deployment type was set to NetScaler ADC when logging in.
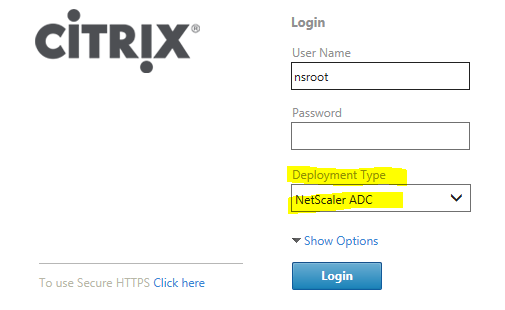
- Navigate to the NetScaler Gateway node. This is when under the Configuration section/tab.
- Click Configure NetScaler Gateway for Enterprise Store.

- In the window that pops-up, click Create New NetScaler Gateway at the upper right.
- Enter a name and IP address for the virtual server. Click Continue.

- Select the Certificate to use as the server certificate for this virtual server. Click Continue.
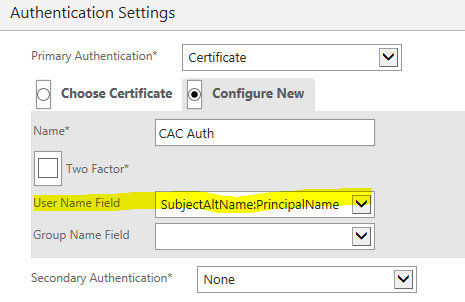
- Set the Primary Authentication to Certificate. If there is an existing certificate authentication profile on the NetScaler for CAC/PIV, select it. If not, select Configure New. The User Name Field needs to be SubjectAltName:PrincipalName. Click Continue.
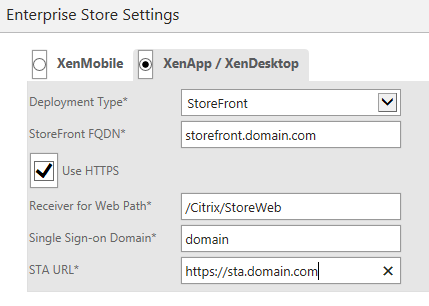
- Set the Enterprise Store Settings to XenApp/XenDesktop. Set the Deployment Type to StoreFront. Enter the StoreFront server and store information. Make sure to use the same STA as in StoreFront. More STAs can be added later. Click Done.
- The pop-up window can now be closed and you will be returned to the NS web management gui (assuming this is still the next window in the background).
Tweaking the Virtual Server
- Navigate to NetScaler Gateway->Virtual Servers. Double-click the virtual server to open it.
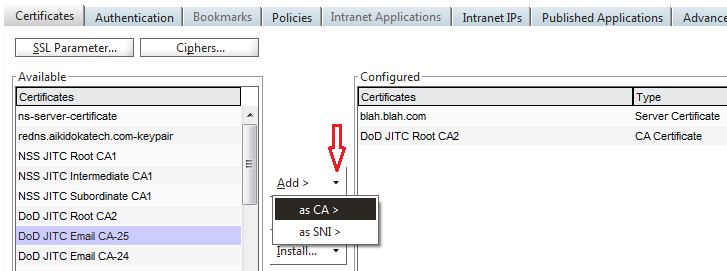
- Under the Certificates tab, use the triangle to the right of the Add button to add each CA required to validate the CAC/PIV cards. All CAs up to and including the root are required. Do not click OK yet!
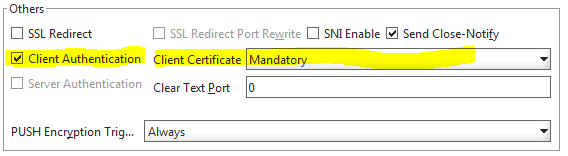
- Still under the Certificates tab click SSL Parameters button. In the Others section check Client Authentication and set Client Certificate to Mandatory. (This causes the requirement for a separate callback URL) Click OK to close the SSL Parameters windows. Do not click OK at the virtual server window yet!
- Under the Policies tab there should be two Session Policies. One will start “PL_WB”. This is for the Receiver for Web. Since Receiver for Web does not yet support smart card authentication, right-click it and unbind the policy. Double-click the policy that starts “PL_OS”. This is for Native Receivers (OS = Operating System).
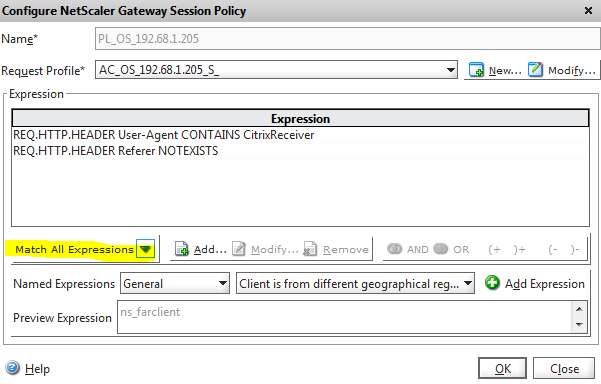
- In the Session Policy, switch the expression rules to Match All Expressions. Do not click OK yet.
- On the Request Profile line, click the Modify button. Make sure the following are set under each tab. Others may also already be set from the wizard.
- Network Configuration tab
- Alter nothing!!!
- Client Experience tab
- Clientless Access – Override Global – Allow
- Plug-In Type – Override Global – Java
- SSON to Web Apps – Override Global – Checked (Credential Index no longer needs to be secondary as with Web Interface setups)
- Security tab
- Default Authorization Action – Override Global – Allow
- Published Applications tab
- ICA Proxy – Override Global – On
- WI Address – Override Global – Base url of SF server (https://FQDN); not path to store also
- SSON Domain – Uncheck Override Global and leave blank.
- Account Services Address – Override Global – Base url of SF server (https://FQDN)
- Network Configuration tab
- Click OK to close the Session Profile window. Click OK to close the Session Policy window. Do not click OK at the virtual server window yet!
- Under the Published Applications tab add any additional STAs that might be needed for the environment. Click OK to close the virtual server window.
Creating the Callback Virtual Server
The callback is used for SSON purposes. Since the virtual server for StoreFront has client certificate set to mandatory, a callback to this URL by StoreFront will be rejected by the NSG as it does not present a client certificate.
- Navigate to NetScaler Gateway->Virtual Servers. Click the Add button.
- Enter a Name and IP for the callback virtual server. Under the Certificates tab, add a server certificate. Click Create when done.
Troubleshooting
- There is an Application log for StoreFront in the Event Viewer. Check there for error messages.
- Make sure all the proper CAs are added to the NSG virtual server to authenticate the CAC/PIV card in use. The entire chain needs to be added.
- Make sure all the proper CAs are installed on the client end device if using Windows. OSX and Linux may have the same requirement. Mobile devices do not.
- Watch the ns.log file on the NetScaler when a client attempts to connect. It can indicate issues such as missing CA certificates. “tail -f /var/log/ns.log” in an SSH session will watch it in real-time.
- Middleware is not needed on the StoreFront server.


